The entire setup was done on FortiOS version 7.4.8. However, it should work on any 7.X build.
The customer wanted to use local DNS servers instead of global DNS servers to point to the local IP address in replies rather than global, the public DNS is 8.8.8.8/1.1.1.1.
Initially we settled this by configuring DNS servers at the VPN>SSL-VPN Settings level and appropriate policies on the firewall (DNS traffic to the LAN port was allowed).
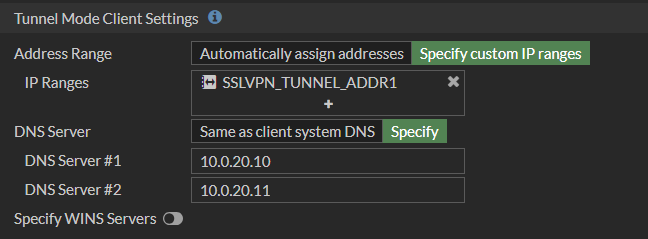
In the next step, the customer wanted the IP addresses of these servers to be hidden, and communication from hosts connected via SSL-VPN to the DNS servers to be impossible.
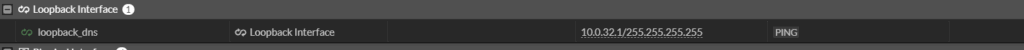
To achieve this, let’s start by creating a loopback interface with the address of our choice.
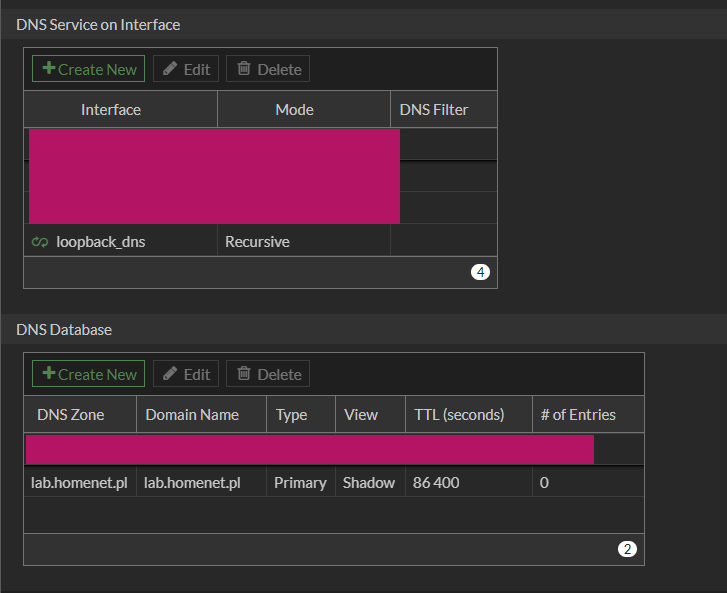
After that, go to Feature Visibility -> Additional Features -> DNS Database and enable the option. DNS Service has been enabled on the interface and the DNS database has been configured. Queries for lab.homenet.pl should be sent to local servers: 10.0.20.10 i 10.0.20.11.
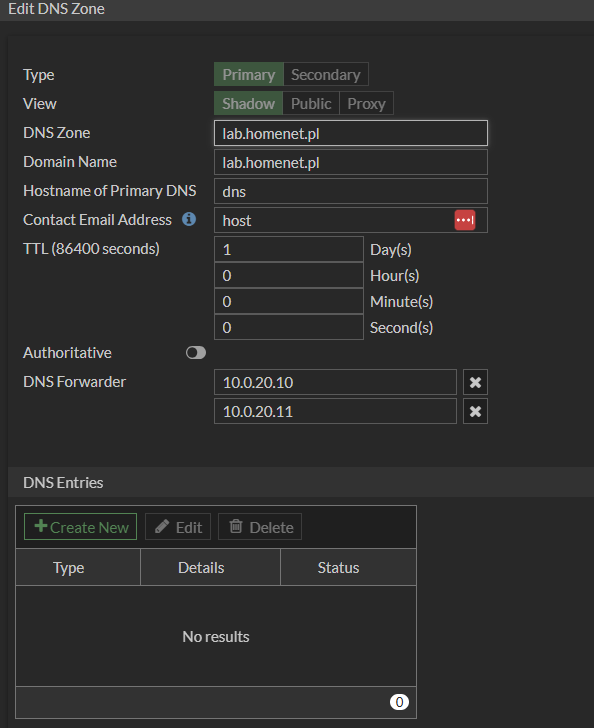
Remember to disable / enable the Authoritative option on a case-by-case basis. In this case, we wanted to disable this option (It depends on whether you accept that FortiGate is the sole source of information for that zone).
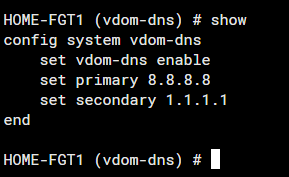
If your fortigate is running in VDOM mode, you need to configure the vdom-dns system option as enable and point to two IP addresses as DNS server addresses.
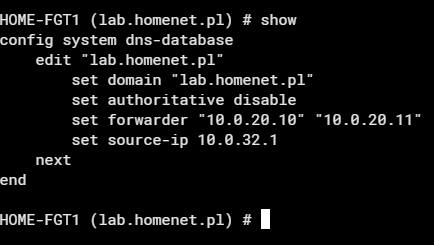
Lastly, to configure the dns database for our domain, we had to indicate the source-ip parameter as the IP address of the loopback_dns interface. The source-ip parameter can only be pointed to an interface in a vdom other than mgmt when using the previously configured vdom-dns option.
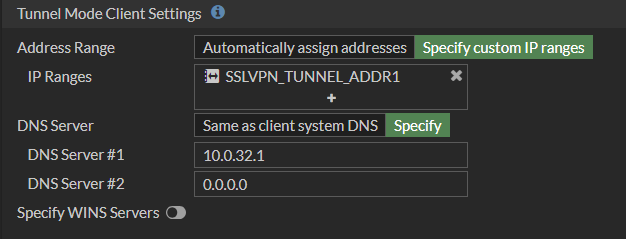
Finally, we change the DNS server at the SSL-VPN settings level:
And that’s it, that’s how you can hide DNS server IPs behind the Fortigat loopback interface.
Sources: