Today I’d like to talk about the security switch that Fortigate has for us when we change its configuration and something goes wrong. Most vendors have that – Juniper has a commit confirmed , Cisco routers have a reload in, Aruba checkpoint auto and Fortinet has one too – cfg-save.
cfg-save is global setting, to use this feature, simply change cfg-save from automatic to revert before making risky changes.
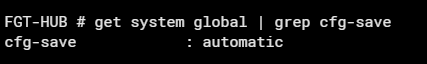
After changing this setting, any configuration change made in the CLI or GUI will take effect immediately (as usual), but will be REVERTED if you don’t save the change manually, and the session will expire. The timeout can also be set with set cfg-revert-timeout .
When restoring changes after a timeout, Fortigate will reload the saved configuration, which means it will not restart, but there will still be a disconnection of all passing sessions. So this configuration restore operation will result in a very short downtime, in my experience – less than a minute if you use BGP with default timers and no BFD it will take a little more.
Config is simple:
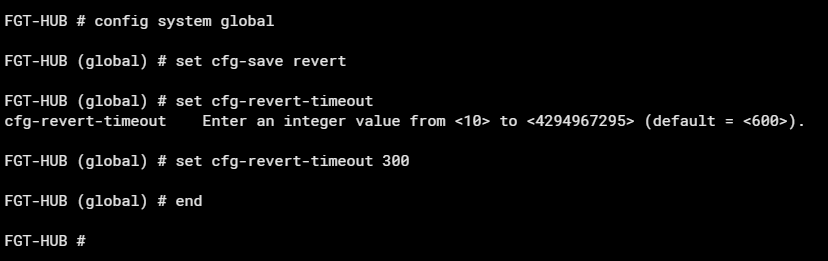
If the changes you made block access to Fortigate and you can’t reconnect, just wait 5 minutes and the changes you made will be restored.
If, on the other hand, you have made changes and nothing bad has happened – do not log out/leave Fortigate. In order for the changes not to be restored 5 minutes after logging out, you need to manually save/confirm them in the configuration file. This can be done on cli:
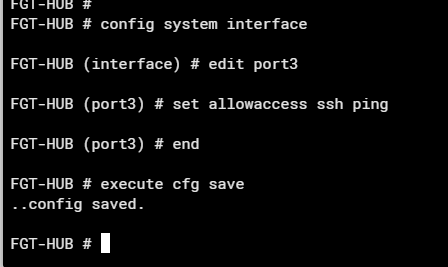
Or the GUI in newer versions of FortiOS:
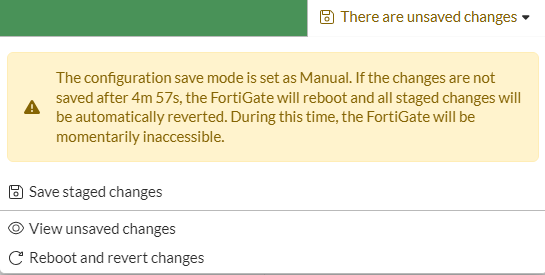
You can also turn on/off this features on GUI in Settings tab
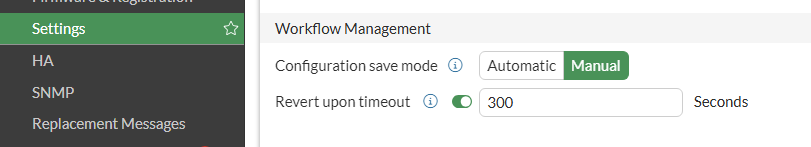
Workspace/workflow GUI is available from FortiOS 7.0 onwards