As you might know SSL VPN on FortiGate soon will be depracated (SSLVPN server functionality is disabled by default on 2G RAM models and IMO it will be diabled for good in a few years). Due to recurring security bugs in SSL libraries, this is considered too much of a problem. To allow easier use, such as in home networks / hotel or cafe restaurant that do not allow UDP, a tcp transport for ipsec has been added.
This forces admins to start moving to other solutions – ZTNA, FortiSASE or IPSEC VPNs. This post is about IPSEC VPNs and what can you do.
My configuraion works and was tested on FortiOS 7.4.7 and FortiClient 7.4.2. There are few option what can you do:
For example, if you currently only use LDAP / S for your AD server, you can configure it in IPSEC using Ikev1 (Xauth only), but it is very limited for the same reason. In this model, for example, you will not use SAML EntraID.
Let’s then focus on Ikev2. Documentation can be found here: https://docs.fortinet.com/document/fortigate/7.4.7/administration-guide/785501/forticlient-as-dialup-client
First, let’s create a radius user group and then a user group that will refer to the corresponding AD group:
config user radius
edit "RAD-SRV1"
set server "169.254.0.10"
set secret ENC set auth-type ms_chap_v2
set source-ip "169.254.1.1"
set require-message-authenticator disable #optional
next
end
config user group
edit "UG_AD_VPN-1"
set member "RAD-SRV1"
config match
edit 1
set server-name "RAD-SRV1"
set group-name "AD_USER_GROUP"
next
end
next
endI put require-message-authenticator because of the vulnerability: https://docs.fortinet.com/document/fortigate/7.4.5/fortios-release-notes/5880/radius-vulnerability Unfortunately, the client for which I am configuring the VPN requires this feature to be disabled.
Below is rest of configuration:
config vpn ipsec phase1-interface
edit "VPN-RA"
set type dynamic
set interface "wan1"
set ike-version 2
set local-gw 198.51.100.1
set peertype any
set net-device disable
set mode-cfg enable
set ipv4-dns-server1 169.254.3.10
set ipv4-dns-server2 169.254.3.11
set proposal aes256-sha256 aes256-sha1
set dpd on-idle
set dhgrp 21
set eap enable
set eap-identity send-request
set transport udp-fallback-tcp #FortiGate dynamically selects the transport mode
set fallback-tcp-threshold 10
set assign-ip-from name
set ipv4-split-include "VPN-RA-USERS_split" #split-tunnel vpn
set ipv4-name "VPN-RA-USERS_range" #IPs for end users
set client-auto-negotiate enable
set client-keep-alive enable
set psksecret ENC
set dpd-retryinterval 60
next
end
config vpn ipsec phase2-interface
edit "VPN-RA"
set phase1name "VPN-RA"
set proposal aes256-sha256 aes256-sha1
set dhgrp 21
set keepalive enable
next
endMore information about encapsulating ESP over TCP here: https://docs.fortinet.com/document/fortigate/7.4.0/new-features/351073/encapsulate-esp-packets-within-tcp-headers-7-4-2
I just set set transport udp-fallback-tcp with a change to the system setting set ike-tcp-port XXX. This will change the communication to TCP/4500 if UDP/ESP packets are blocked by ISP. I had some problems with S2S VPN after changing this port from 4500, so I left it as is.
Now configure some firewall rules that use the VPN-RA interface as the source interface, remember to put the source user groups / IP addresses in the source field.
Okay, all ready. You can configure Forticlient to connect
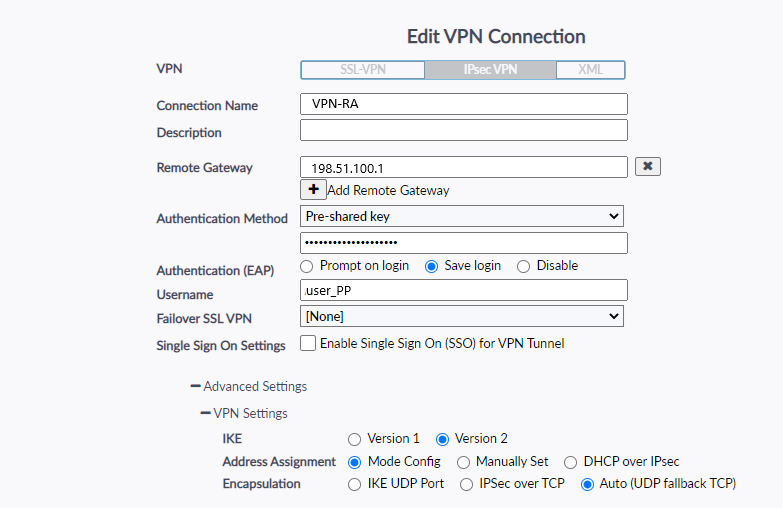
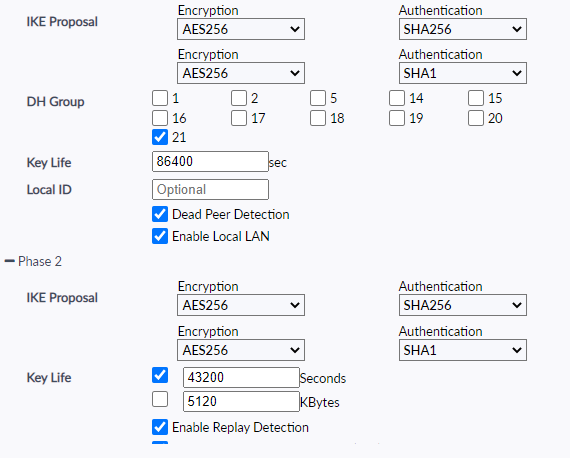
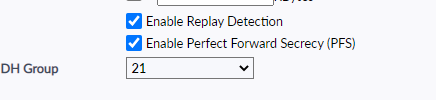
I also had a problem where FortiClient was connecting successfully, but was adding the route 0.0.0.0/0 with the same metric as my own gateway in my routing table, nothing works then 😉 I removed FortiClient, rebooted, reinstalled and that fixed it.