So let’s assume that for some reason you want to check the speed from Fortigate to some host – it could be a server on the local network, it could also be a server in some public cloud.
Fortigate has a built-in iperf3 client and a limited iperf3 server. You can access these functions from the CLI, if you have VDOMs enabled, the commands are accessible from the global vdom.
By default, FortiGate uses TCP for that. It is possible to run UDP with flag -u, but if you do, you should also set the bandwidth with the -b flag.
Also note that for realistic results u should use more parrallel data streams, it can be configured with flag -P <value>.
All options can be checked with diag traffictest run -h command.
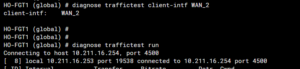
Ok, let’s start with iperf3 for the WAN connection. The configuration will look as follows:
diag traffictest client-intf <string> – Define a FortiGate interface.
diag traffictest server-intf <string> – Define a FortiGate interface.
diag traffictest port <port_num> – Define the iPerf3 port running on the server.
diag traffictest run -c <IP_ADDR> – Run iPerf3
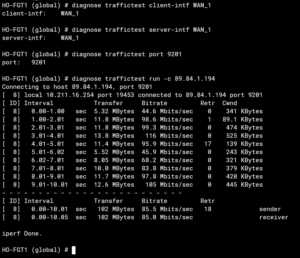
If we want to use a different iperf server, we need to set the client and server intf to the same port. In the image above, you can see that I’m using the WAN_1 interface – this is an EMAC Vlan that I’ve configured under the physical wan interface, which has no IP address assigned.
This is important to keep in mind – interfaces must be assigned an IP address.
Another use case is to run iperf between fortigate ports – to test the basic functions of the device. Just set up the server and client interfaces and run the test.
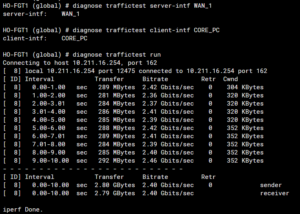
In the image above, traffic is initiated from the CORE_PC interface – this is the vlan under port “a” on my fortigate, the target server is vlan WAN_1, which is under the physical interface “wan”.
Both VLANs are at the same VDOM.
If you want to test iperf between virtual domains, you will need the right routing and security rules to allow traffic
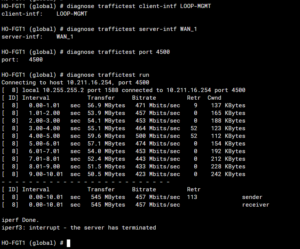
Note that I chose the LOOP-MGMT interface as the client’s intf – this is the loopback interface on the vdom root and has an IP address of 10.0.99.254. Nevertheless, you can see that the local IP address is set to 10.255.255.2 – this is the IP address of the VDOM link.
It appears that fortigate will select the source interface based on the routing table if the interface is of the loopback type.
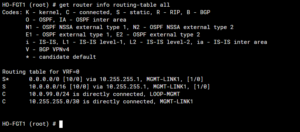
If I choose a vlan interface as the intf client, the local IP address is not changed (WAN_2 is the EMAC Vlan in vdom root).