Hi, This one is to show how you can use automation stitches in your infratructure. Okay, imagine you have a case where you have a VPN to a 3rd party company over which you have no control. You also have two internet connections on your side. And now you want to take advantage of that so you put up a VPN, the third party company only provides you with one public IP on its side. You get two VPNs in this case: LOCAL_ISP1 <-> 3rd_Party and LOCAL_ISP2 <-> 3rd_Party. Okay, you put some routing on both sides – static routing , BGP or whatever you want and everything is ready, you can close the application.
This is a standard implementation, but it happens that sometimes we can’t control everything and do as we want. In this case, imagine that 3rd party tells you that only one tunnel can be active at a time, if they are both then the whole network at their place will go crazy and they will have to fix it for a long time. With the solution comes automation stitches.
Documentation: https://docs.fortinet.com/document/fortigate/7.4.7/administration-guide/139441/automation-stitches
First lets create link monitor that will ping 192.168.1.10 server with source ip 10.0.0.1. We will use logs from status change to trigger automation snitch.
config system link-monitor
edit "VPN-3RD_PRIMARY"
set server "192.168.1.10"
set gateway-ip 10.0.0.1
set source-ip 10.0.0.1
set update-policy-route disable
set service-detection enable
next
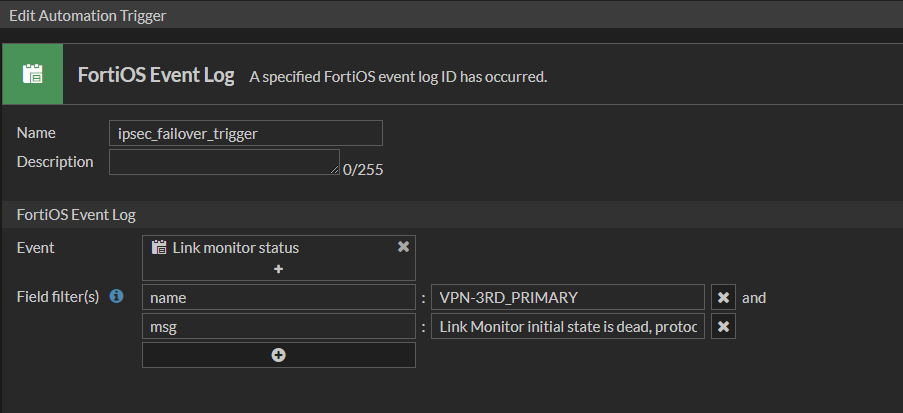
endGo to Security Fabric -> Trigger and create new trigger. Select Event type Link monitor status and two field filters – name and msg. In name field type name of link-monitor object that we created earlier. In msg box type “Link Monitor initial state is dead, protocol: ping”
Now let’s start the first action for our stitch. The email type allows you to inform, for example, the NET department that something is wrong and what change has been made. You can also make MS Teams notifications and many more.
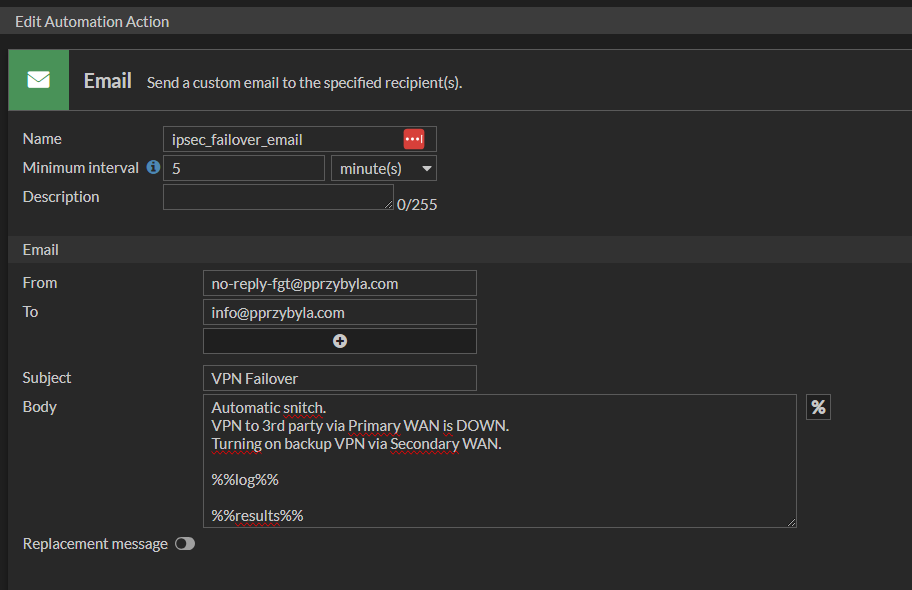
Now lets make CLI Script. It will got to primary VPN interface, shutdown it and then bring up secondary VPN.

Finally, let’s put it all together. We have such a cool Stitch:
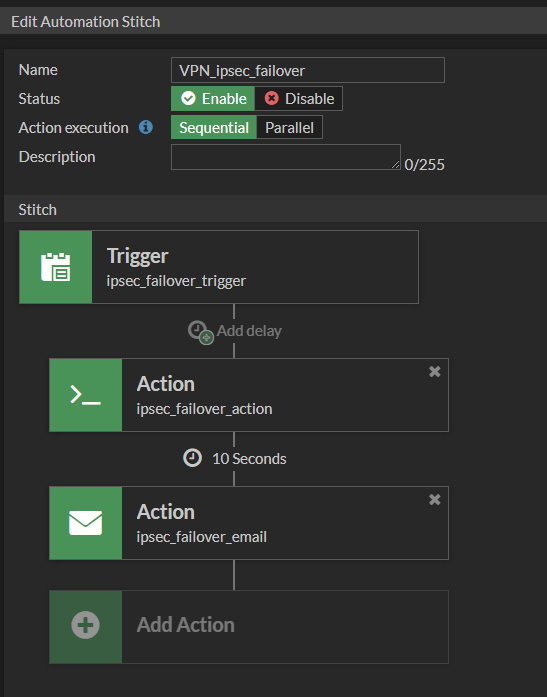
And that’s it, if there is an emergency switchover, the connection will work on the secondary WAN. In the appropriate time window – e.g. in the evening you can switch the vpn back to the primary connection and check if the connection is working. In this scenario you simply do shutdown secondary vpn and no shutdown primary vpn